- Home
- Related Work
- Threat Levels to Space Systems
Threat Levels to Space Systems
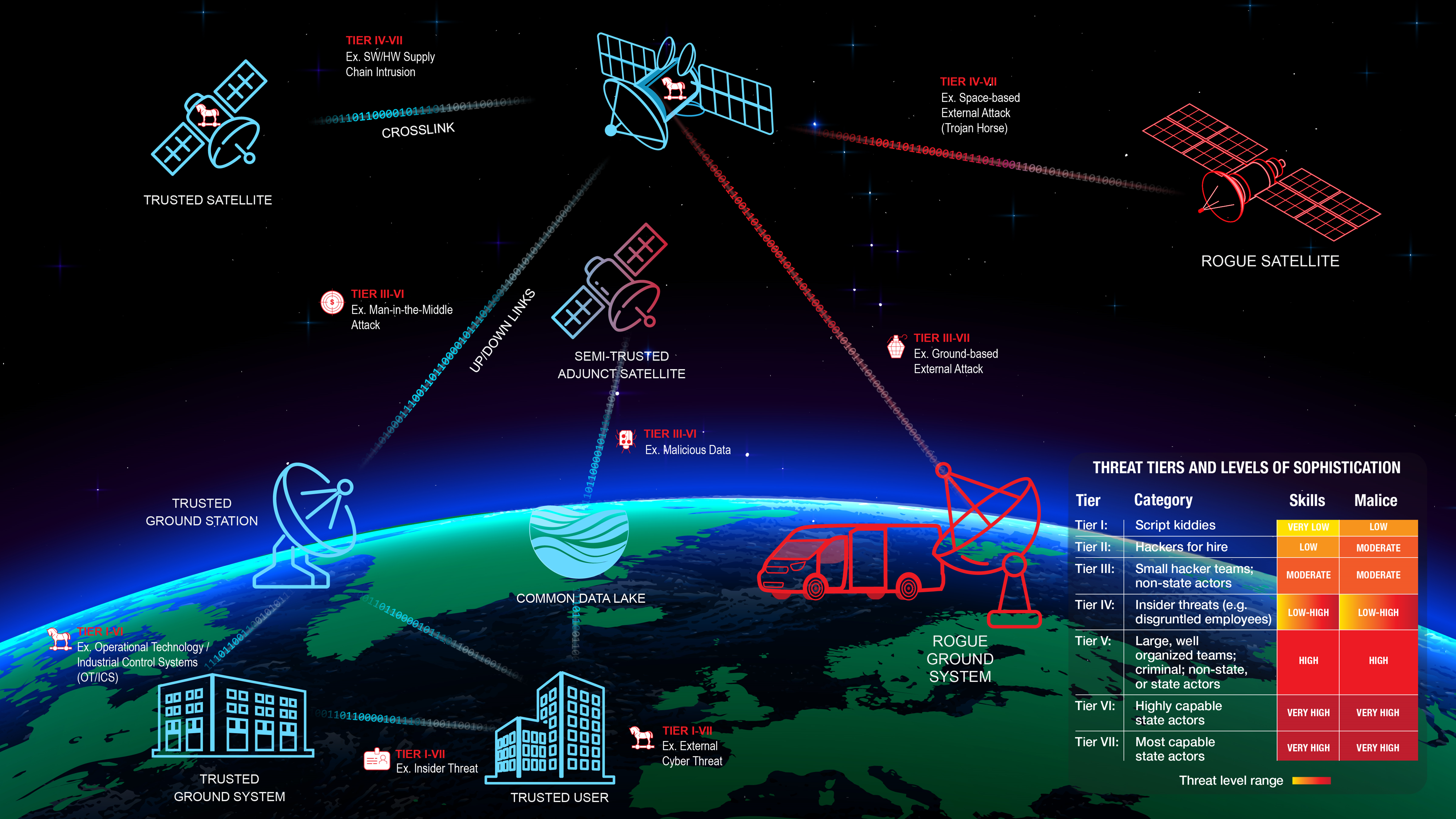
Using a pre-defined, tiered adversary system to calculate likelihood in combination with an unclassified threat model, an example security baseline can be established. Cyber threat likelihood includes aspects such as exploitation difficulty, motivation, and adversary capabilities. The motivation and exploitation difficulty would be program dependent, but the adversary capabilities can be analyzed using a generic approach.
The following table outlines the cyber threat vectors, including their skill level, motivation, and methods:

| Tier | Name | Skills | Maliciousness | Motivation | Methods |
|---|---|---|---|---|---|
| I | Script Kiddies | Very low | Low | Boredom, thrill seeking | Download and run already-written hacking scripts known as “toolkits” |
| II | Hackers for Hire | Low | Moderate | Prestige, personal gain, thrill seeking | Write own scripts, engage in malicious acts, brag about exploits |
| III | Small Hacker Teams, Non-State Actors OR Disorganized/Non-Advanced State Actors | Moderate | Moderate | Power, prestige, intellectual gain, respect | Write scripts and automated tools | IV | Insider Threats (e.g., disgruntled employees) | Very Low – Very High | Very Low – Very High | Unwitting, ideology, politics, espionage | Insider knowledge lowers the barrier of entry. Methods span the spectrum from simple to sophisticated. |
| V | Large, Well-Organized Teams, Criminal, Non-State, or State Actors | High | High | Personal gain, greed, revenge | Sophisticated attacks by criminal/thieves, may be “guns for hire” or involved in organized crime |
| VI | Highly Capable State Actors | Very high | Very high | Ideology, politics, espionage | State sponsored, well-funded cyberattacks against enemy nations |
| VII | Most Capable State Actors |
- Ability to Access Networks
- Ability to Discover & Exploit Vulnerabilities
- Ability to Defeat Crypto & Authentication
- Command & Control Sophistication
- Ability to Affect Cyber/Physical Systems
- Ability to Gain Physical Access
- Sophistication of Human Influence
The resulting analysis is reflected in an updated threats vectors diagram with a threat tier overlay as shown below. This diagram can assist in understanding the adversary levels a program could face for specific threat vectors. Not every program will have to be resilient and mitigate threats across Tier I-VII. For example, a program may have a 90-day mission with a small budget and may choose to accept the risk that a Tier IV-VII adversary could successfully end their mission. This program will still want to mitigate threats vectors tied to Tier I-III.