Notional Risk Scores
In August of 2023 with version 1.4 of SPARTA, the Aerospace Corporation developed and incorporated space cyber Notional Risk Scores (NRS) into the SPARTA framework, associating a notional evaluation of attack techniques leveraging a risk matrix. The intention of NRS is to provide practitioners with a starting point for space cyber risk management, from which they can apply specific details (e.g., a reference architecture) to tailor NRS to evaluate their particular space cyber risks. NRS is a starting point for space developers and other approaches could be used to ensure less subjectivity as described in the paper title, Towards Principled Risk Scores for Space Cyber Risk Management. However, when performing risk assessments in a generic sense for a space system as SPARTA has done, subjectivity and subject matter expertise must be used in lieu of mission specific technical details.
There are multiple tailoring considerations that SPARTA NRS does not reflect, which should be considered to reduce subjectivity and increase mission specific applicability:
- specific architectures/technologies
- existence of specific sub-systems/functions
- mission objectives and the components critical to their success
- mission importance of confidentiality, integrity, and availability of data
- mission-specific threat intelligence (including geo-political developments or future plans that might increase the likelihood of adversarial action)
NRS was built on previous work published in Aerospace Report TOR-2021-01333-REV A which details a generic threat model and risk assessment approach that considers a high-level view of adversary capabilities and ranks them into threat tiers. Given the difficulty of establishing the likelihood of an attack due to the uniqueness of every mission and system implementation, threat tiers are leveraged to illustrate adversary capability. The threat tiers indicate the capabilities required to inform likelihood that an actor can execute certain SPARTA techniques.
At a high level, NRS provides a risk scoring matrix for each SPARTA technique based on system criticality. Risk scores are determined by (i) likelihood of successful execution of technique and (ii) impact incurred.
System Criticality: There are three categories in system criticality: high, associated with systems related to critical functions, military purposes, and intelligence activities; medium, associated with civil, science, weather, and commercial systems; and, low, associated with academic and research systems. Subject matter experts assigned a risk score for each SPARTA technique at each system criticality level. The built in assumption for this criticality approach is a high criticality system is a more attractive target (i.e., motivation is higher) than a low criticality system.
SPARTA Technique Likelihood: The evaluation of technique likelihood includes three aspects: (i) adversary motivation, influenced by the system criticality with the assumption that adversaries are more motivated to attack high criticality rather than low criticality systems; (ii) exploitation difficulty, based on technique complexity; and, (iii) adversary capabilities, according to the following seven threat tiers, in increasing order: script kiddies, hackers for hire, small hacker teams, insider threats, large well-organized teams, highly capable state actors, and most capable state actors. Subjective analysis on these three aspects provides the overall likelihood score which results in a range from 1 to 5}.
SPARTA Technique Impact: The impact of a technique against a space system refers to the consequences, effects, or outcomes resulting from the successful execution of the technique. Subjective analysis considers wide ranging impact that may include mission disruption, data integrity compromise, loss of control or availability, financial consequences, safety, or even national security implications. Impact is also defined in a range from 1 to 5}.
Risk Matrix Representation (Risk Scores): The resulting impact and likelihood is a representation of the notional risk scores of the SPARTA techniques on a 5x5 risk matrix. The matrix provides a risk score with respect to an assessed impact score from 1 to 5 (the x-axis) and a likelihood score from 1 to 5 (the y-axis); the risk scores are shown in the respective cells of the matrix and reflect the joint effect of impact and likelihood, according to the 5×5 matrix defined in NASA-S3001: Guidance for Risk Management.
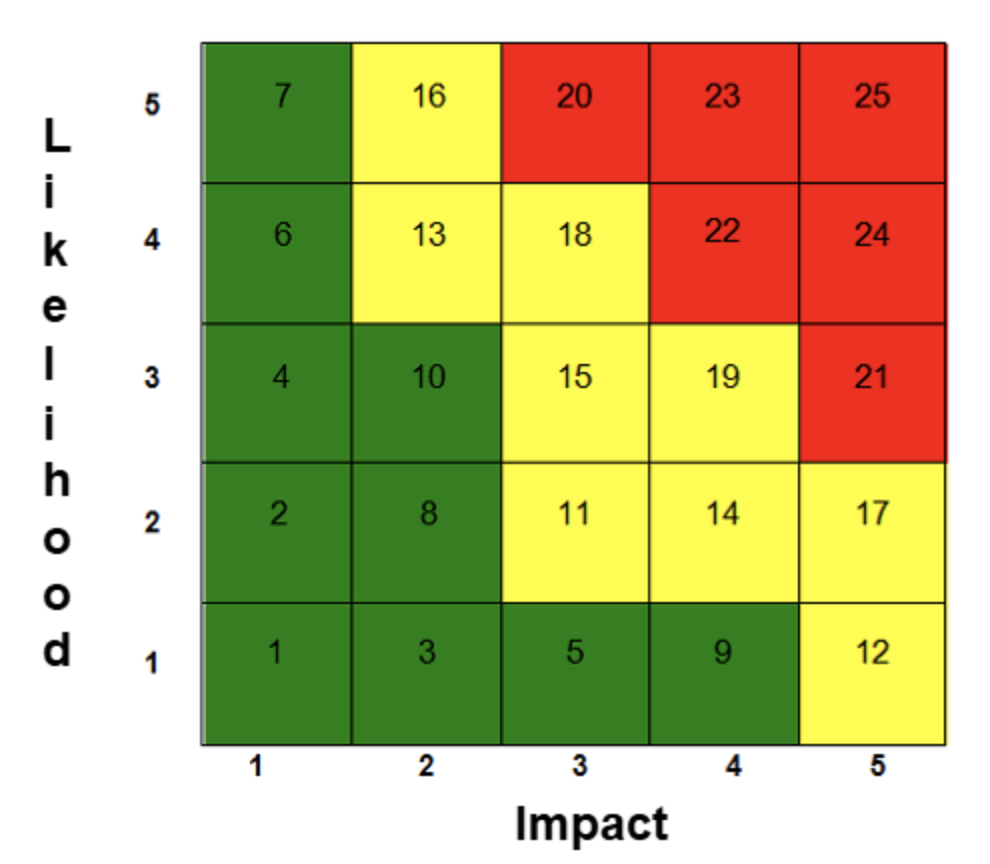
Risk scores range from 1 to 25 but are not the product of likelihood and impact. The scores are a result of which cell the technique falls under after using the respective 1 to 5 score for both likelihood and impact. Risk scores ranging from 1 to 10 are considered low (green), 11 to 19 considered medium (yellow), and 20 to 25 considered high (red). Ranging from 1-25, each of these three distinct values are presented on the applicable SPARTA TTP pages as Notional Risk (H | M | L): HighRisk # | MediumRisk # | LowRisk #.
As with all SPARTA content, this process and the notional scores are expected to evolve over time. There are plans to implement future functionality to allow more tailoring within the tool to better reflect system/mission-specific parameters. For the time being, it is up to SPARTA users to consider additional tailoring that should take place so that these notional scores are adjusted to reflect their own unique mission.
NRS Tailoring
Algorithm 1 within this paper, describes the expected method for tailoring/using NRS within the context of a specific mission.
Input: Taking the applicable SPARTA techniques; leverage the existing NRS base risk score R, which is a set indexed by technique with element RA being the basic risk score of technique A; a set indexed by SPARTA technique with element CA being a set of countermeasures to technique A; a set indexed by countermeasure, with element ScA being a set of countermeasure cA ∈ CA; specific environment/conditions of the space system; tolerable risk threshold τ ∈ {‘low′, ‘medium′, ‘high′}.
Output: a set of security controls/countermeasures that must be employed to mitigate intolerable risks and awareness of techniques that may be high risk to the mission in question.
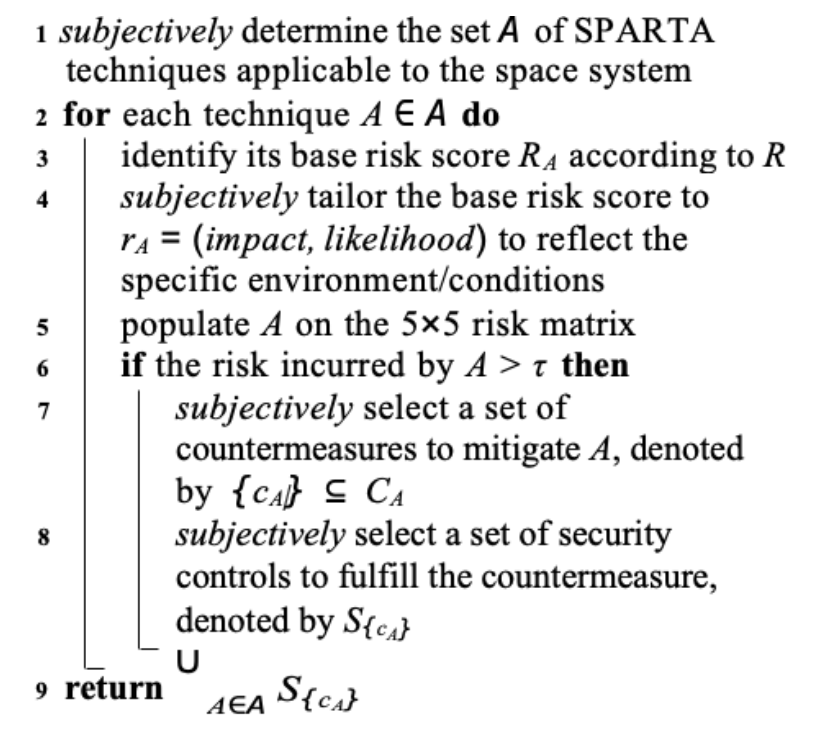
The above algorithm shows how to use NRS to quantify space cyber risk and identify mitigations. Line 1 determines the SPARTA techniques that can incur risk to the space infrastructure/system in question. Lines 2-9 assess each applicable technique, where: lines 3-5 generate the tailored risk score associated with each applicable SPARTA technique, by determining the impact and likelihood of each technique according to the specific environment/conditions of the space infrastructure/system and mapping it to the 5×5 risk matrix; and, lines 6- 9 determine if a SPARTA technique is tolerable; if not, select countermeasures and security controls to mitigate the intolerable SPARTA techniques.
Essentially, take the SPARTA techniques applicable to a specific system and the associated base NRS score as the starting point, then factor in mission-specific risk tolerance and the mission’s existing countermeasures to come up with mission-specific impact and likelihood. When countermeasures do not exist, then add additional countermeasures until the tolerable risk threshold is reached.
Below are example notional risk scores within SPARTA, which is a starting point for SPARTA users to understand high risk techniques to their system. These scores should be tailored as previously described. The following Excel Spreadsheet has all of the default NRS scores to include the 5x5 risk score and the applicable impact and likelihood scores.